Details
-
Type:
 extRequest
extRequest
-
Status: Closed
-
Priority:
 Major
Major
-
Resolution: Done
-
Fix Version/s: 2021
-
Component/s: FIWARE-TECH-HELP
-
Labels:None
Description
Hi!
I have been battling with this on and off all week following every tutorial both video and written I can find, but whatever I try I have not been able to get past "User not authorized in application" even though I am convinced my test user is authorized to use the application.
I am using the lab tutorials.PEP-Proxy docker containers for this exercise without Authzforce - I do not believe we need a complicated level of authorization at this stage and so I want to keep things as simple as possible.
Here are my steps:
Using Keyrock GUI:
<http://www.chalmers.se>
1. Create user
2. Create application with PEP proxy but do not add new user as authorized user to application at this stage:
[cid:8637e033-50b3-4adb-9fed-5a085a71120c]
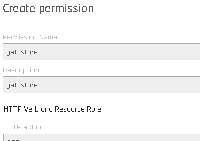
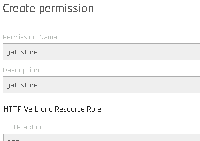
3. Create simple new permission "get-store" and assign to new role "test-get":
[cid:b6742e0b-4151-4a6e-91e9-6694f70a075e]
In a terminal:
4. using the new application client_id and client_secret, create an authorization token:
$ echo -n client_id:client_secret | base64 -w 0
NjU5Zm...DmU1Nw==
5. using the authorization token from step 4, the user's email address as the username and the user's password, generate an access token:
$ curl -X POST 'http://localhost:3005/oauth2/token' -H 'Accept: application/json' -H 'Authorization: Basic NjU5ZmQyND.........mU1Nw==' -H 'Content-Type: application/x-www-form-urlencoded' --data "username=user@email.com&password=password&grant_type=password"
6. Check if user authorized for application - as expected: "authorization_decision":"Deny"
$ curl -X GET 'http://localhost:3005/user?access_token=edd91b...e35e00&action=GET&resource=/v2/entities/test&app_id=application_client_id'
{"organizations":[],"displayName":"","roles":[],"app_id":"application_client_id","trusted_apps":[],"isGravatarEnabled":"","id":"user_id","authorization_decision":"Deny","app_azf_domain":"","eidas_profile":{},"attributes":{},"shared_attributes":"","username":"username","email":"user@email.com","image":"","gravatar":"","extra":""}
7. Now (in Keyrock GUI) add new user as authorized user with role "test-get" to the application and check again - now: "authorization_decision":"Permit" for role "test-get"
$ curl -X GET 'http://localhost:3005/user?access_token=edd91b...e35e00&action=GET&resource=/v2/entities/test&app_id=application_client_id'
{"organizations":[],"displayName":"","roles":[
],"app_id":"app_id","trusted_apps":[],"isGravatarEnabled":"","id":"user_id","authorization_decision":"Permit","app_azf_domain":"","eidas_profile":{},"attributes":{},"shared_attributes":"","username":"username","email":"user@email.com","image":"","gravatar":"","extra":""}
8. Back in a terminal as user, attempt to retrieve store information:
$ curl -iX GET http://localhost:1027/v2/entities/urn:ngsi-ld:Store:001 -H 'X-Auth-token: edd91b...e35e00'
HTTP/1.1 401 Unauthorized
...
User not authorized in application
pep-orion-proxy log shows:
2021-02-26T08:20:35.204 - INFO: IDM-Client - Checking token with IDM...
2021-02-26T08:20:35.225 - ERROR: IDM-Client - Error in IDM communication "User not authorized in application"
2021-02-26T08:20:35.226 - ERROR: Root - User not authorized in application
keyrock log shows:
ri, 26 Feb 2021 08:21:10 GMT idm:oauth_controller --> authenticate_token
Fri, 26 Feb 2021 08:21:10 GMT idm:oauth_controller --> authenticate_bearer
Fri, 26 Feb 2021 08:21:10 GMT idm:oauth2-model_oauth_server ------getAccesToken------
Fri, 26 Feb 2021 08:21:10 GMT idm:oauth2-model_oauth_server ------create_oauth_response------
Fri, 26 Feb 2021 08:21:10 GMT idm:oauth2-model_oauth_server ------search_user_info------
Fri, 26 Feb 2021 08:21:10 GMT idm:oauth2-model_oauth_server ------trusted_applications------
Fri, 26 Feb 2021 08:21:10 GMT idm:oauth2-model_oauth_server ------user_roles------
Fri, 26 Feb 2021 08:21:10 GMT idm:oauth2-model_oauth_server ------user_permissions------
Fri, 26 Feb 2021 08:21:10 GMT idm:oauth_controller Error
I'm sure I'm missing something but I'm not sure exactly what - please can you help me get over this hurdle?
Thank you so much!
Taz
__________________________________________________________________________________________
You can get more information about our cookies and privacy policies on the following links:
fiware-tech-help mailing list
fiware-tech-help@lists.fiware.org
To unsubscribe from fiware-tech-help mailing list, go to the information page of the list at:
https://lists.fiware.org/listinfo/fiware-tech-help
[Created via e-mail received from: Taz Lodder <taz@chalmers.se>]


It seems that the tutorial's service script has been updated to create the service groups on start-up. The POST request is correct if no service group had been corrected. The text has been amended as shown:
—
IoT Agent - provisioning a trusted service group
The Access token (also known as a Trust Token) must be added to the service group. The `resource` and `apikey` correspond
{ "apikey": "1068318794", "cbroker": "http://orion:1026", "entity_type": "Motion", "resource": "/iot/d", }to the values set-up within the service group provisioning stage. In this case the Motion sensor group had been provisioned
as shown:
18 Request:
curl -iX PUT \
{ "cbroker": "http://orion-proxy:1027", "trust": "30a5ce4c71e416bd199dcdcb7f8bcd8d70e8bb5e" }'http://localhost:4041/iot/services?resource=/iot/d&apikey=1068318794' \
-H 'Content-Type: application/json' \
-H 'fiware-service: openiot' \
-H 'fiware-servicepath: /' \
-d '
'
The Motion sensor requests are now sent via the `orion-proxy` and identify themselves using the generated trust token.